Single sign-on (SAML SSO)
Integrating Userflow with your identity provider (such as Okta or OneLogin) makes signing in simple and secure for your team.
Important: SAML SSO is only available as an add-on to Pro or as a part of Userflow’s Enterprise plan (see plans).
Once SSO is enabled, Userflow’s sign-in form will automatically detect your domain, and let your users to sign in via your identity provider.
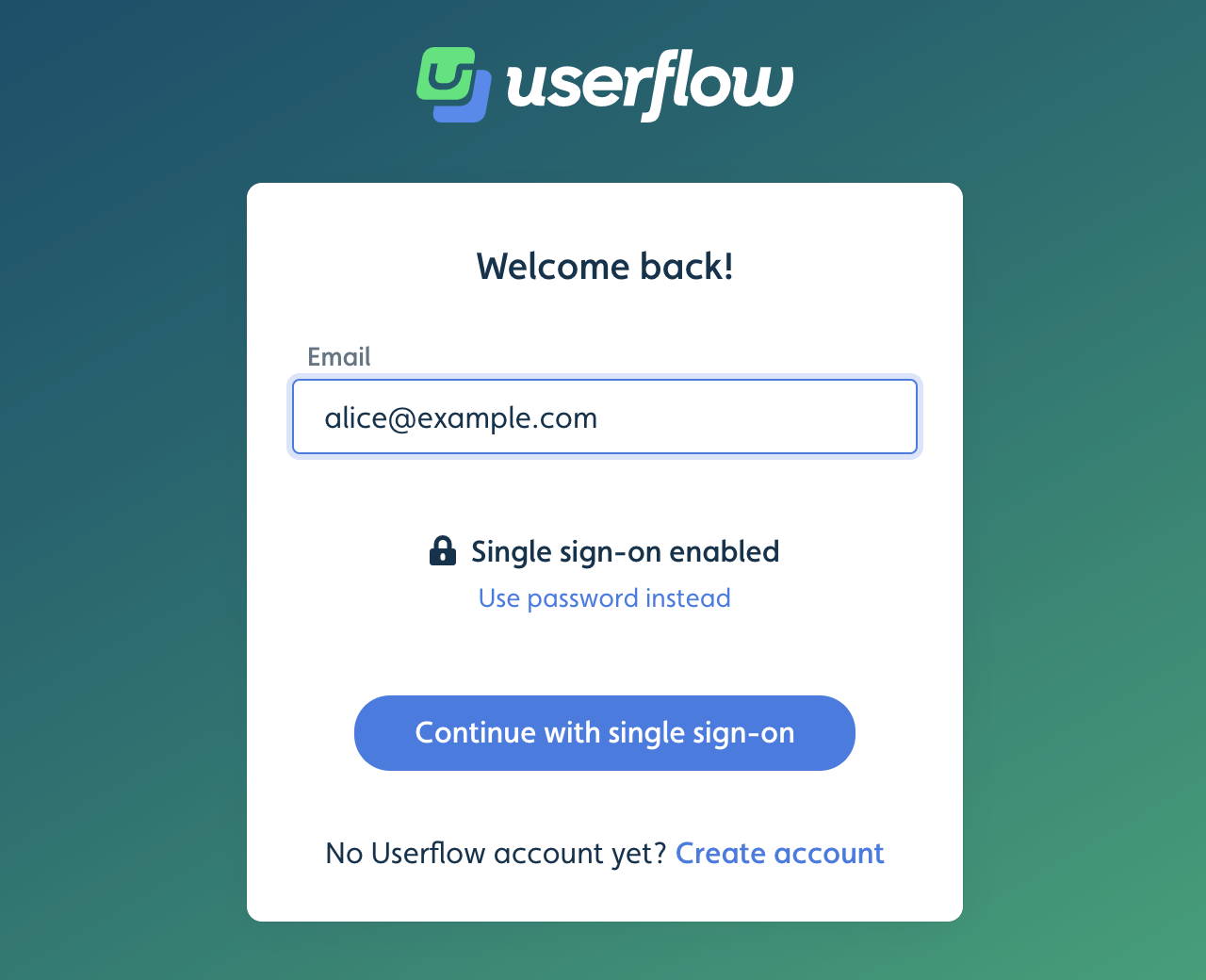
Setup instructions
Step 1: Obtain your Customer ID from Userflow
Send an email to support@userflow.com with the following information:
- That you wish to enable SAML SSO for your Userflow team
- Your company name
- Domain(s) your users sign in with
We’ll get back to you (typically within 24 hours) with your Customer ID, which you need to complete the following steps.
Step 2: Configure your identity provider
Okta
For easy setup with Okta, see How to Configure SAML 2.0 for Userflow in Okta.
Generic SAML identity provider
Make sure to replace CUSTOMER_ID with the value Userflow provided.
-
Single sign on URL / SAML ACS URL:
https://userflow.com/sso/sp/consume/CUSTOMER_ID - Audience URI / SP Entity ID: userflow
-
Default RelayState:
https://userflow.com/app - Name ID format: EmailAddress
- Application username: Email
- Signed Assertions: Yes
- Encryption: Preferred. Use AES256-CBC with this certificate
-
Single Logout URL:
https://userflow.com/sso/sp/logout/CUSTOMER_ID - SP Issuer: userflow
- Signature Certificate: Use this certificate
-
Mapped Attributes
-
email: User’s email -
firstName: User’s first name -
lastName: User’s last name
-
Step 3: Send Identity Provider metadata XML file to Userflow
Download your identify provider’s Identity Provider metadata XML file and send it to support@userflow.com.
We’ll finish the setup for you, and let you know once SSO is enabled for your domain(s).
Working with SSO
Existing users with passwords
Users that were registered in Userflow before you enabled SSO, can sign in either via SSO or using their old password.
Contact us to disable password access for specific users after SSO is set up.
Adding members to your Userflow team
You can invite new members to your Userflow team under Settings -> Team. They’ll receive an invite link. The invite page automatically detects that SSO is available. Once they sign in via SSO, they’ll have access to your team.
You can also add team members outside of your Identity Provider organization. These users can create regular Userflow user accounts using password sign-in.
Just-in-time (JIT) user provisioning
When a new user, which Userflow hasn’t seen before, signs in via SSO, Userflow automatically creates an account for them.
The new user will NOT get access to your Userflow team though. They still need an explicit invite.
User de-provisioning
When users are deactivated/removed in your Identity Provider, they are not automatically removed from your Userflow team.
However, since users not using password must sign in via SSO, once you remove their authorization in your Identity Provider they will no longer be able to access your Userflow team (once their current session, if any, expires after 30 minutes of inactivity).
To be sure, you can always remove team members in Userflow under Settings -> Team.
Userflow’s SAML certificate
If you configure your Identity Provider manually, you’ll need this certificate to enable encryption and Single Logout.
You can either download the certificate or copy it from here:
-----BEGIN CERTIFICATE-----
MIIDVjCCAj6gAwIBAgIUCtL81BwLSLWkeW9xPX5SlA4kyEwwDQYJKoZIhvcNAQEL
BQAwMDEWMBQGA1UEAwwNVXNlcmZsb3cgU0FNTDEWMBQGA1UECgwNVXNlcmZsb3cs
IEluYzAeFw0yNTAxMDYwNTExMzlaFw0zMDAxMDUwNTExMzlaMDAxFjAUBgNVBAMM
DVVzZXJmbG93IFNBTUwxFjAUBgNVBAoMDVVzZXJmbG93LCBJbmMwggEiMA0GCSqG
SIb3DQEBAQUAA4IBDwAwggEKAoIBAQDf41jxxETESJFF35nsTE1SDp4kz8QZ0M8J
jiBQzc+9deY8pxqABTjBAHreIVLiq3CdHc411xgO6orZTLvZFalkoVkwFS4jfQE5
kU5m7+ucOq62q3ENv4CJKZaN/PTwnVEw8mTsPVb9s1nzIw+PBABJnJXNTVPOuPRN
TyitzUwj+8Y0CqYK+cE8xjT+Eo0DtoBzLmWU5nkqyr1/MQUiGzvDrybJfD2XQqRe
8mbqC+JTfR48b37vTIOjIrjxYPbWRU5cjAiS0EgyGHK9SUzjuFXOKPfPic8VhShB
rmmCv1FqR0I+bEdf1xSLDMbskywG5PfnLejWyjMY7hcNkCrEGLfPAgMBAAGjaDBm
MB0GA1UdDgQWBBR7spJceWpV+ONY9ZkBcczRuXt2aTAfBgNVHSMEGDAWgBR7spJc
eWpV+ONY9ZkBcczRuXt2aTAPBgNVHRMBAf8EBTADAQH/MBMGA1UdEQQMMAqCCHVz
ZXJmbG93MA0GCSqGSIb3DQEBCwUAA4IBAQAJ0aa/fd6PpwFm3YwKcNsNhtKTplJv
+Zra/pRNDaFIf55rf79Ug/527SugoWEWXysgj7az3Sz9Nc3JgWCWt+XGYAaKXBwB
G64d3PDuNwfE3WP4tEeikuzTUYY89Vm/AVQcffPZDClAi/7JOSCMzRZHuUpP27eY
uyq44aSkTOnnn69aKIuACv1a8dNMkOA3R8+ollgvexFI9VcnT+PMam++UVpooL+V
JBeTJ01lHk9K0hqqF2fvAmcb4SanoHzkN67UOnY67GHcuTn3ACtB8E1GhZdjED9L
LTRNtM8RQ3c0Yo/yjzFnzYnlm7A7vGZWmTotLlZmDn+teVTvWV1XRRcX
-----END CERTIFICATE-----